These days, the protection of privacy and security on the Internet is more relevant than ever, and Pretty Good Privacy (PGP) is considered an essential tool for encrypting communications and ensuring the integrity of information. Since its creation, PGP has not only provided a solid defense against computer spying, but has also come to symbolize the fight for privacy in the digital world.
The purpose of this article is to be an in-depth look at the history, operation, and current importance of PGP in cybersecurity.
What is PGP encryption?
PGP is a data encryption system based on public key cryptography designed to protect information transmitted over the Internet. In addition to its ability to encrypt messages and files, PGP allows documents to be authenticated and their integrity to be verified through digital signatures, ensuring that the information has not been altered and that it comes from a legitimate source.
PGP is based on a pair of keys: a public key, which is shared with other users to encrypt messages, and a private key, which remains secret and is needed to decrypt received messages.
PGP History, development, and controversies
PGP was first released in 1991 by Phil Zimmermann, who developed the software as part of his commitment to protecting individual privacy in the digital age. The name “Pretty Good Privacy” was inspired by a fictional business mentioned on an American radio show, and reflected the pragmatic and accessible nature Zimmermann wanted to give his software.
The launch coincided with a time when strong encryption systems, those with keys larger than 40 bits, were classified as “weapons” by the U.S. government. At the time, any encryption technology with a key size greater than 40 bits was considered dangerous as a weapon and therefore strictly prohibited from being exported without a license under the Arms Export Control Act.
The controversy intensified when PGP became freely available on the Internet, giving people outside the United States unrestricted access to a powerful encryption technology. The U.S. government began a criminal investigation of Zimmermann in 1993, accusing him of “exporting munitions without a license“. The act of making PGP available on the Internet was interpreted as a violation of these export regulations.
Despite the seriousness of the allegations, the investigation was ultimately closed in 1996 without formal charges being filed. This outcome underscored the growing importance of encryption as a privacy tool and the legal challenges privacy advocates face in a world where the lines between national security and individual rights are increasingly blurred.
Cryptographic fundamentals
PGP uses a hybrid approach that combines symmetric and asymmetric encryption to optimize both security and efficiency:
- Symmetric encryption: PGP generates a unique session key to encrypt the contents of the message or file. Algorithms such as AES (Advanced Encryption Standard) are commonly used because of their high level of security and efficiency.
- Asymmetric encryption: The session key is encrypted with the recipient’s public key, ensuring that only the recipient can decrypt the content with their private key.
- Digital signature: PGP enables the creation of digital signatures to guarantee that messages or files have not been altered and that they originate from the legitimate sender. This is achieved by encrypting a hash of the content with the sender’s private key.
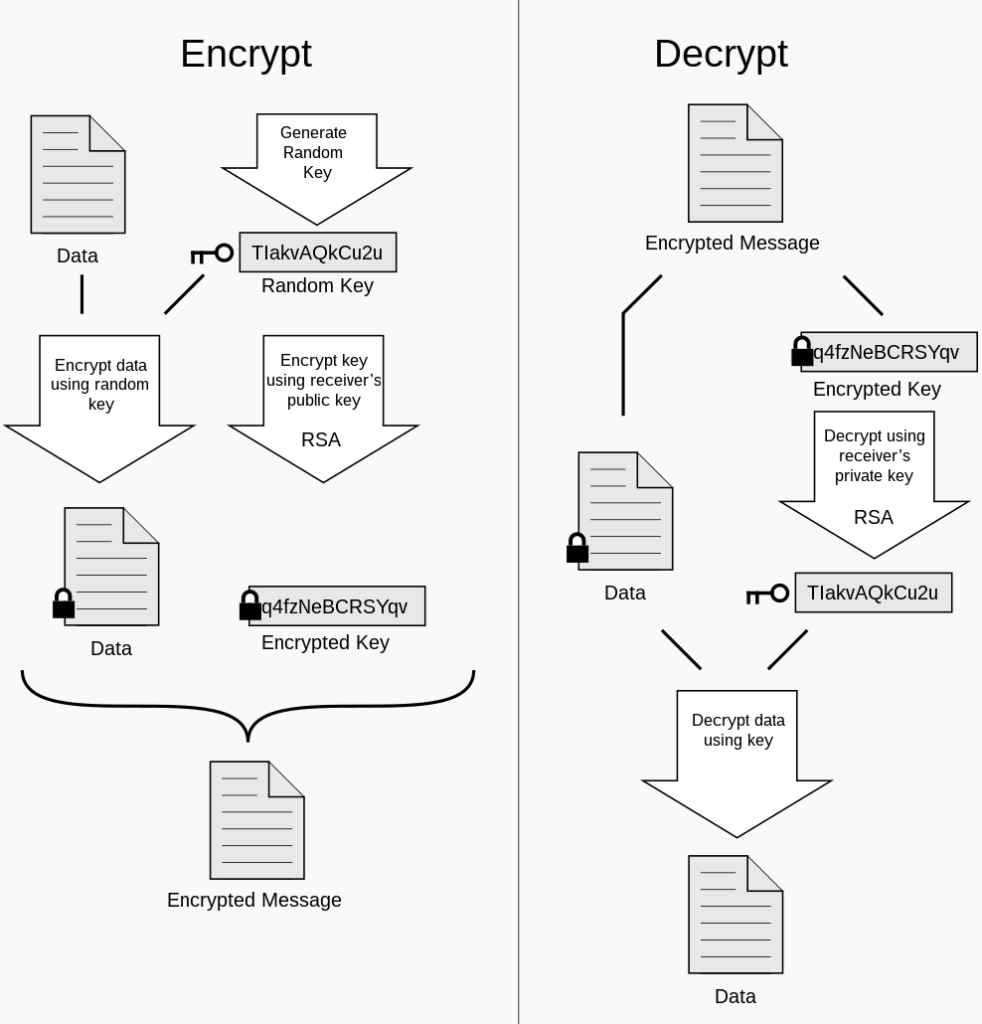
How PGP works?
PGP encryption protects data using a combination of public keys, private keys, and session keys. The encryption and decryption process can be broken down into the following steps:
- Sesion key generation: PGP generates a unique, random session key that is used to encrypt the contents of the message.
- Message encryption: The message is encrypted using the generated session key. This method of symmetric encryption is efficient and ensures that only those who have the session key can decrypt the contents.
- Session key encryption: The session key is encrypted with the recipient’s public key, ensuring that only the recipient can decrypt it with their private key.
- Send and decrypt the message: The recipient receives the encrypted message along with the encrypted session key. Using his or her private key, the recipient decrypts the session key and then decrypts the original message.
This approach combines the speed of symmetric encryption with the robustness of asymmetric encryption, providing an effective solution for protecting information.
Importance of the network of trust and digital signatures
One of the distinguishing features of PGP is the concept of a “network of trust. This mechanism allows users to sign the public keys of others, indicating that they trust the identity of the key owner. When multiple trusted individuals sign a key, it is considered trustworthy without the need for a central authority, as is common in traditional Public Key Infrastructure (PKI) systems.
Digital signatures also play an important role in PGP. When a message is digitally signed, the sender creates a hash of the content and encrypts it with his or her private key. The recipient can verify the signature using the sender’s public key; if the hash matches, the authenticity and integrity of the message is confirmed.
The difference between encrypted content and encrypted connections
A common misconception is that email is fully encrypted when sent over SSL/TLS. However, SSL/TLS only encrypts the transmission channel, protecting the message in transit, but not its content once it is stored on the server.
In contrast, PGP encrypts the content of the message, ensuring that even if it is intercepted, it cannot be read without the proper key. In addition, PGP allows the message to be digitally signed, ensuring its authenticity and protecting it from unauthorized modification.
Examples of PGP encryption usage
PGP encryption has been adopted in many areas, including:
- Encrypting confidential messages: PGP is widely used to encrypt email and protect sensitive information in electronic communications.
- File and file system encryption: PGP is also used to encrypt files on disks or servers to ensure the privacy of stored information.
- Digital signatures: PGP uses digital signatures to authenticate and verify the integrity of programs, documents, and other files.
- PGP fingerprint: A fingerprint is a reduced version of a public key that is used to verify its authenticity and prevent attacks from intermediaries.
PGP as an Internet standard: OpenPGP
Over time, Zimmermann recognized the need to establish an open standard for PGP. For this reason, in 1997 he proposed to the Internet Engineering Task Force (IETF) the creation of OpenPGP, a standard that allows interoperability between different encryption software implementations. In 1999, Werner Koch developed GnuPG (GPG), a free implementation of OpenPGP that has been widely adopted for its open source nature and free availability.
GnuPG: The free alternative to PGP
Although PGP became a paid solution after its acquisition by Symantec in 2010, GNU Privacy Guard (GnuPG) was developed as a free, OpenPGP-compatible alternative. GnuPG allows users to download, modify and use the software free of charge, guaranteeing access to robust encryption tools.
Key differences between PGP and GPG
Despite their similarities, PGP and GPG differ in two important ways:
- Licensing: PGP is proprietary software, while GPG is open source and free. This means that PGP generally requires a paid license, while GPG is freely available.
- Support: PGP provides technical support through an official portal, while GPG relies on the community and third-party vendors for support.
Tips for using PGP or GPG effectively
- Private key protection: Never share your PGP private key, and keep it in a safe place.
- Software updates: Keep your software up to date to mitigate potential vulnerabilities.
- Verificación de claves públicas: Always verify the authenticity of the other party’s public key before using it.
- Use strong passphrases: Protect your PGP key with a strong, unique passphrase.
Conclusion
PGP remains a fundamental tool for security and privacy in the digital age. Despite technical and legal challenges, and the emergence of new technologies, PGP provides a high level of security when used correctly. With a proper understanding of its operation and key management, users can rely on PGP as a robust solution for protecting sensitive information in an increasingly digital world.
Resources:
[1] Wikipedia – Pretty Good Privacy
[2] Varonis.com – PGP Encryption
[3] Jscape – PGP vs GPG
At Block&Capital, specialists in tech recruitment, we strive to create an environment where growth and success are within everyone’s reach. If you’re ready to take your career to the next level, we encourage you to join us.
Last posts